Distribution
Guide to WebRTC CDN for Distribution of Streaming Content
The Dolby.io Streaming Content Delivery Network (CDN) offers a range of server-side features that users can toggle and adjust via the REST APIs or your account Dashboard to ensure streams are secure, stable, and scalable.
✓ Scalability to distribute content to large audiences across multiple regions in real-time.
✓ Stability with features like simulcast with WebRTC that provide redundancy and adaptability to maintain a good user experience across different network and device conditions while maintaining a high uptime and Quality of Experience (QoE).
✓ Security through features that protect your content by securing streams with subscriber tokens, self-signed tokens, allowing only specific origins, geo-blocking, and IP filtering.
Distribution of streaming content requires scalability, stability, and security along with a robust platform with features including stream recordings, multi-source broadcasting, multi-bitrate delivery, backup publishing, stream syndication, and streaming analytics.
Start building
Distribution of streaming content
Distribution of high-value content and intellectual property requires a platform that values security, stability, and scalability.
Security
How-to Manage Your Tokens
Tokens are generated to authenticate and give access to a stream for a specific period of time. You will use separate tokens for publishing and subscribing to a stream so that only appropriate authorizations are granted depending on your requirements, such as:
- Specifying specific domain names or allowed origins
- Identifying IP addresses to filter
How-to Setup Geo-blocking
Geo-blocking can be enabled to block specific geographic areas, such as countries or regions where you do not want the content to be streamed.
Stability
Whether the stream has one viewer or hundreds of thousands, the stability of the stream is a top priority. To support stream stability and adaptability, Dolby.io provides several important features.
Multi-source streaming
Add redundancy with multiple independent broadcast sources as part of the same stream. This distribution of multiple audio and video tracks enables the viewer to playback a different feed in case an incoming source becomes unavailable.
Audio multiplexing
With multiplexing, this enables end users to receive multiple audio feeds as part of a single broadcast such that viewers can toggle between different audio tracks, such as variations in language, quality, etc.
Simulcast
Simulcast is a mechanism that allows for the distribution of a media stream composed of multiple bitrates and resolutions. The user can then view a stream that has a quality determined by network or device type allowing low-bandwidth conditions to receive an appropriate quality stream for the most stable experience possible in that scenario.
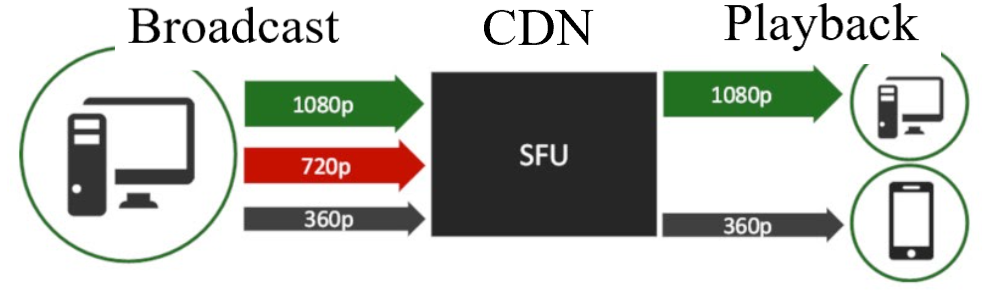
Figure: Broadcast multiple resolutions in order to optimize playback for each device.
Backup publishing
Similar to multi-source streaming, backup publishing allows for a parallel broadcast to be ingested from the same encoding source. In case of a failure, the system can fall over to another active backup stream.
Scalability
To support global audiences into the hundreds of thousands of viewers, Dolby.io provides features that help with scaling streams to meet those demands without impacting the quality or stability of the stream.
Multi-region support
We utilize a network of data centers distributed around the globe. This allows streams to maintain ultra-low latency and high scalability to audiences that may be scattered to many different regions.
Stream syndication
Through distribution partners, syndication allows you to send the same stream to multiple platforms. A tracking id can be used to correlate and analyze distribution data to monitor bandwidth utilization, viewer attendance with each provider, and other statistics that can help with billing.
Recordings
A live broadcast can be archived by enabling the storage of a recording of the stream.
Self-signed tokens
To improve performance when tracking many individual streams among your users, you only need to generate one Dolby.io token and can then delegate that authorization by generating new self-signed JWT tokens in your application without needing to fetch a new subscriber token from Dolby.io for each new stream.
Streaming analytics
The Dolby.io dashboard provides data-rich information about streaming usage for your individual account. There are also REST and GraphQL endpoints to generate custom reports and behaviors by querying that data.
Learn more
Updated 16 days ago